BCACTF 3.0
BCACTF 3.0
麻了,之前的没保存全没了…
这个比赛给的提示是真的多。难度不打,很适合我 😃。
MISC
Sequence
1 | |
提示是著名的数列之一。google看了一下应该是雷卡曼数列,前面几项也能对的上。完成生成数列函数即可。
1 | |
Blender Creation
下载下来是一张图片,二进制查看可以看到末尾有一段python代码。dump出来看看。
1 | |
中间的a就是我们的flag。
1 | |
x的值可以算,前面的base64也可以解。接出来就是bcactf{所以这里就是我们的flag。那么我们还需要得到yrsth这个部分。
1 | |
u的的话相当于直接给出了。中间几段明文跑一下就能得到。可以的得到以下代码:
1 | |
可以看到前面有一个blender这个单词。所以猜测缺少的一个是1一个是3。
后面有一个0次方,所以是0。
1 | |
你看看那个单词像不像python?后面加了85所以应该是Y。那么yrsth就是:
1 | |
Gogle Maze
是一个google文档。但是我们啥都做不了,点击下一个没用。
右键查看源代码。搜索bcactf。
找到flag。
1 | |
Crypto
New Keyboard
1 | |
提示说他用了一个少见的键盘格式。
猜测
1 | |
是我们的flag。
找了一下应该是这个Dvorak键盘:
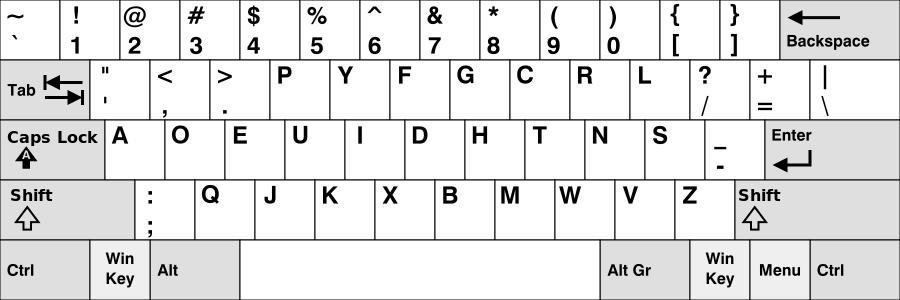
因为unai的位置刚好就是我们正常键盘的flag。所以flag为:
1 | |
Hidden Frequencies
文件是一串字符
1 | |
统计每个字符出现的次数,然后转ascii。
1 | |
Really Secure Algorithm
1 | |
标准的rsa。
直接解就行了。
1 | |
这里输出的m就是我们的明文,只不过他不是16进制的,而是10进制的。提示里说他喜欢十进制我也是半天没理解。
如果你看m的十进制输出的话,可以看到开头是98999799这个其实就是ascii码了, b(98)c(99)a(97)c(99)。
Funky Factors
1 | |
啥都没给,一般来说就是n可以直接分解。
1 | |
得到p,q。解rsa即可。
1 | |
Salty
看名字估计就是哈希了。
给的是个网站,里面的debug部分给出了一个hash和salt。题目描述是4位数字和小写字母。那么我们来爆破。
1 | |
1 | |
之后使用admin登录。
1 | |
A Fine Line
1 | |
下载下来里面是一串字符,提示说是放射密码。然后码表也给我们了。提示二说两个字符解下一个字符。所以就可以得到解法了。
放射密码一共有三个参数,一个乘数一个加数和一个模数。模数实际上是码表的长度,所以是固定的。那么两个字符解下一个其实就是两个字符作为乘数和加数。
1 | |
嗯…好像不太对。
最后发现是我们对提示的理解错了,我以为是两个字符解下一个字符,实际上是两个字符解下两个字符…而且算法写的也有点问题,改一下。
1 | |
本博客所有文章除特别声明外,均采用 CC BY-SA 4.0 协议 ,转载请注明出处!